Hacking wifi network or protection from hacking?
Hacking wifi network or protection from hacking?
This statte we re-describe way to capture packets from the wifi network with which you can pick up the password or key to the wifi network.
The last time we helped FOR AirSlax. Now we will do the seizure by Kali system.
To start downloading the image of Kali Linux system, you can even download for example a lightweight version of “Kali Linux 64 bit Light”. images can be downloaded from the page of the official site.
Once the image has to be here, to fill the stick, the program will help us Universal-USB-Installer-1.9.6.9
We kindly uploaded it on our website to be a long time looking for the world wide web. Run the application, and specify the path to the image of Kali.
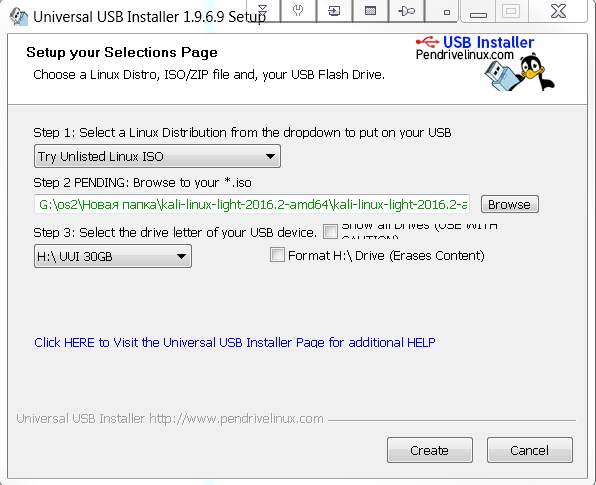 That’s about to be looking for a program ready to burn an image on a usb storage device (USB flash drive). Then click Create and wait until the image is written to the flash drive.
That’s about to be looking for a program ready to burn an image on a usb storage device (USB flash drive). Then click Create and wait until the image is written to the flash drive.
A few minutes passed, the image recorded. Close the window to save documents supercharged and insert the flash drive into the usb port.
When downloading, select Live option (amd64) and expect a full system boot.
Enter data for the authorization, root login and password toor. We offer a select dialog menu system, select the “Use default config”.
At the bottom of the dialog appears, click on the terminal and translate the map in monitor mode:
ifconfig wlan0 down && iwconfig wlan0 mode monitor && ifconfig wlan0 up
Look for the available access point attack
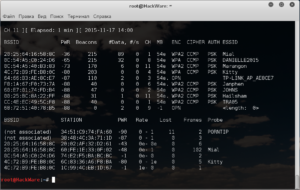
airodump-ng wlan0
Choosing for example network Mial, её ВSSID 20:25:64:16:58:8C on the channel 1. That is why we are launching airodump-ng on the first channel
airodump-ng wlan0 –channel 1 -w cap2
After -w key goes cap2 prefix file (this name without extension). This file is written to the captured handshake.
You can do nothing – just wait until someone connects or reconnects in a natural way. If you hurry, you can speed up the process using deauthentication attack.
To do this, we open a new terminal window and type the command there:
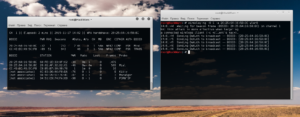
aireplay-ng -0 5 -a 20:25:64:16:58:8C wlan0
There is deauthentication -0, 5 means the number of packets sent, -a 20: 25: 64 16: 58: 8C is BSSID target TD and wlan0 – network interface in monitor mode.
The result was not long in coming:
Inscription«WPA handshake: 20:25:64:16:58:8C» It tells us that the handshake is already captured.
We are sure that this is true:
ls -l cap*.cap
The directory will be displayed our captured handshake
Then, the data packets from the WiFi network is transferred to the page Restore passwords for WIFI networks
And check on the fortress of our wifi network.
Thanks also hackware portal for the help 🙂
 English
English Русский
Русский